NEWS 
Lords of the keys to the world internet. Who are they and what do they do

Four times a year, two dozen people meet to conduct some kind of ceremony. These meetings were no different from regular office meetings, if not for the unprecedented security measures that participants go through before getting there: biometric scanners, retina and fingerprint scanners are just a few of them. The reason why they are collected is also not the most commonplace: some of them are the custodians of the unique key to the global Internet. Together, their keys form a master key that controls one of the main security measures at the heart of the Internet - the Domain Name System (DNS).
First ICANN ceremony. Source ICANN
What is DNS
You can open any site on the Internet by entering its numeric IP address or symbolic name in the browser line. It is more convenient for us to use the second option, and the first for the machine, so we need an intermediary that would convert characters from domains to IP addresses. Behind this there is a domain name system - DNS (Domain Name System). It stores and manages information about domain zones.
For ease of understanding, DNS is compared to a phone book that stores contact names (URLs) and their phone numbers (IP addresses). DNS does not exist in virtual space, but on certain physical servers with special software.
How DNS Server Works
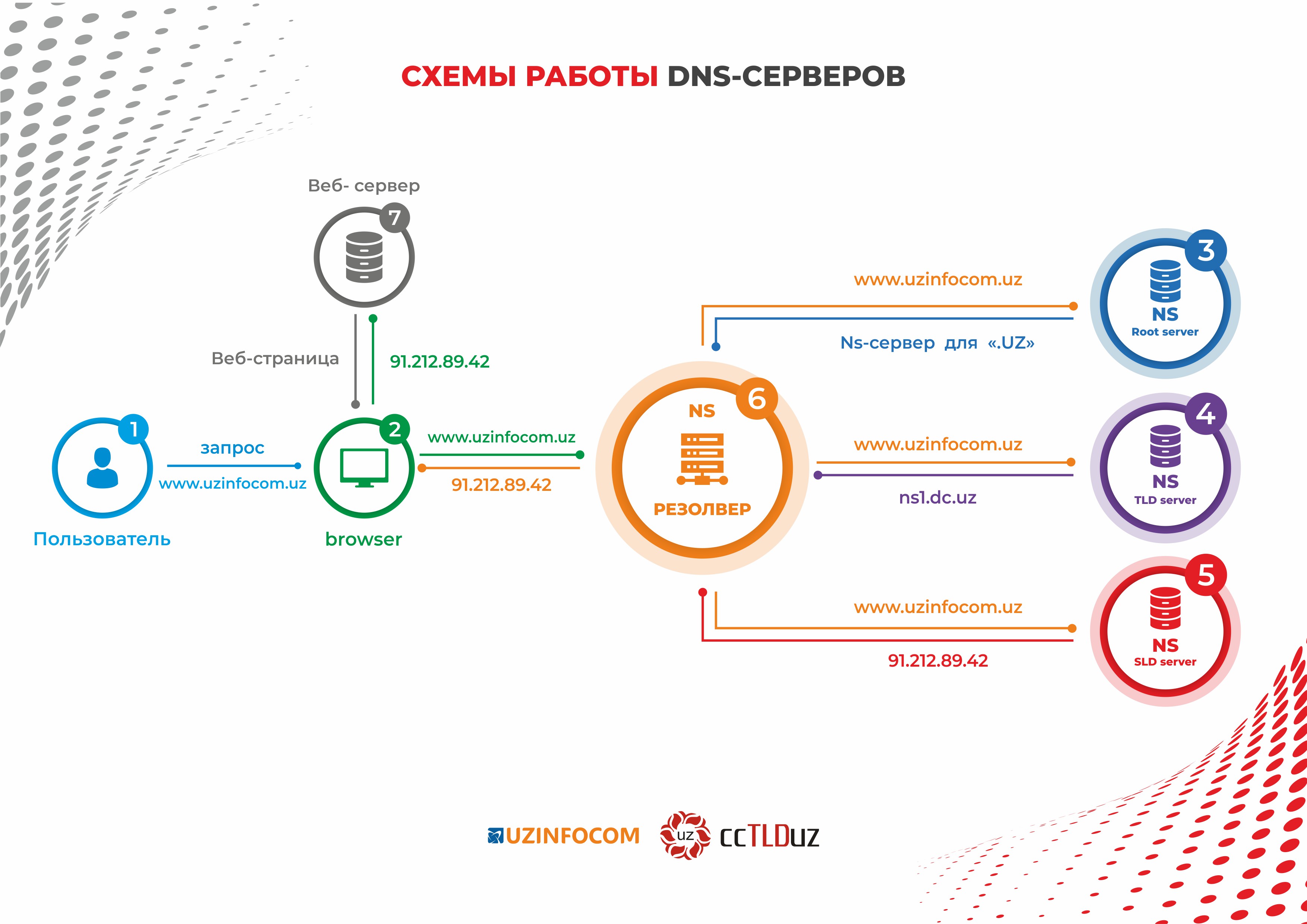
The browser receives a request from the user and forwards it to the DNS server on the network, which looks for a match between the domain name and the network address. If the answer is found, then the site page is loaded immediately. Otherwise, the request is sent to the upstream server or root.
The root server forwards the request to the first-level server, which in turn passes it on to the second-level server. This movement continues until a match is found between the name and IP address.
The browser receives a response to its request, directs it to the hosting, and the page opens.
Where are the DNS servers
The root servers responsible for the root DNS zone are the foundation for processing all queries for domain names. There are 13 root servers around the world, and they are managed by different operators under agreements with ICANN. These include universities, US Department of Defense organizations, and non-profit associations. 10 servers are located in the USA, three more in the Netherlands, Sweden and Japan. In addition to the 13 root servers, there are hundreds of duplicate root servers. All operators are legally and financially independent from ICANN, so no organization controls the entire system.
Key verification ceremony
ICANN was created in 1998 with the participation of the US government as an organization for regulating issues related to domain names and other aspects of the functioning of the Internet. Since 2016, she has become independent. A system developed in the company using a master key and its distributed storage is part of the global measures to ensure the security of the Internet.

Source Tim Hales / AP
Since 2010, key holders have met four times a year, twice on the US East Coast and twice on the West Coast, to update keys and make sure the Network is secure. Key Keepers are a select group of security experts, renowned community members from all over the world. They were chosen based on experience and geographical location - no country is allowed to control too many keys to avoid centralizing power in one hand.
These men and women control the system at the heart of the network: the Domain Name System (DNS). Each time the custodians meet, they authenticate every entry in these online address books. Spoofing IP addresses can lead people to malicious sites used to hack computers or steal data.
During the "ritual", a new master key is generated, which is then activated using smart cards, signed by the custodians, and loaded onto USB drives for servers in various domain zones (.com, .net, etc.).
There are seven key holders at each of the East and West Coast ceremonies, and seven more people around the world have the authority to re-establish the system if anything goes wrong. Each of the 14 primary key holders (seven on each coast) has a traditional metal safe key that holds a smart card, which in turn activates the device that creates a new master key.

Photo: cloudflare.com
In the event of an emergency, the "safeguard" 7 keeps smart cards containing a piece of code needed to create a new master key generator. Once a year, these seven people send selfies to ICANN with the newspaper for the current date and their key to confirm that they are okay.
The initial selection process for key keepers was surprisingly subtle: the company announced the recruitment of participants on its website and received only 40 applications for 21 positions. The list of event participants is publicly available and has changed little since the first ceremony.
How is the ceremony
The West Coast ceremony takes place in an inconspicuous industrial area outside Los Angeles, in a protected area. There are a minimum of windows inside the building, there are no windows at all in the ceremony hall, a bunch of sensors, scanners and cameras. Even to get into the cafeteria, you have to go through a door that requires a pin code, smart card and biometric hand scan. Then you will find yourself in a small room in which only one door can be opened at a time. Then comes another sequence of smart cards, handprints and codes to exit.
Neither guards nor cleaning ladies are allowed into the main hall, so the key keepers themselves pre-prepare it for the event. The ceremony itself is a plan of more than 100 points, written down to the minute, each deviation from which is noted in the official protocol, which everyone present must later read and sign.
Access inside opens only after a retinal scan of an authorized ICANN staff member. Then the participants in the procession find themselves in a space reminiscent of a doctor's office: several rows of bolted metal chairs, and opposite a table. On the other side of the room is a cage with two high security safes. Under the ceiling are cameras broadcasting live on the ICANN website.
One of the employees and the key holders (at least three are required for the ceremony, not all seven) enter the secure cage to retrieve their smart cards, which are stored in the safe in special tamper-evident bags.
After that, the staff sets up the computer, connects several USB drives to it, one of which is used at the end of the ceremony to upload the signed key to the Internet: the code will be uploaded to the servers that determine who controls the various domain zones .com, .net, etc.

Source flickr / Olaf Kolkman
Then the device that will generate the master key is configured - a hardware and software cryptographic module (HSM). It is a simple little gray box with a keyboard and card slot on the front. If dropped, or even shaken too hard, it will destroy the keys stored inside. It is activated with smart cards that the keepers have just taken from the safe.
Each custodian hands over his smart card, the device is activated, several lines of program code are entered into it, which generate a new digital key. The USB stick is then handed over to another ICANN staff member who will later pass on the key over a secure channel and post it online. It will be valid for three months - until the next ceremony.
After generating a new key, the keepers return to the cage with the safes in which their smart cards are stored in order to put them back in place.

Source: flickr / Olaf Kolkman
What happens if you lose access to all crypto keys at once
In itself, this is unlikely, because the keys are stored on four HSMs in safes in two highly secured sites located 4,000 km apart (on the East and West coasts). However, ICANN also maintains encrypted backups for each root zone key. If all 4 HSM modules fail, the company will order a new module from the manufacturer and restore keys from backups. In this case, a special ceremony will be held in the presence of additional trusted community representatives and “keepers of the backup key portions”.
The Internet is much more than just DNSSEC extensions. It consists of many different systems, and DNS is just one of them. Controlling one aspect of how the Internet works, such as the DNS, does not mean having complete control over every other aspect.









